LICADHO Clarifies Hacking Attack Report
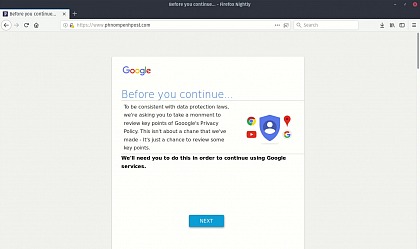
Published on 17 May 2018Last week, LICADHO staff discovered a strange phenomenon when trying to access the Phnom Penh Post website. When visiting the site, a malicious code impersonating Google (misspelled Gooogle) attempted to trick users into granting full access to their Gmail inboxes to an unknown third party called GTransfers.
LICADHO analysed the code which was hidden within a legitimate script file (theme.js) hosted on the Phnom Penh Post website and forwarded its findings to partners in the region. The tampering with the website was independently confirmed by cyber security experts - including industry leader FireEye - in an ABC article.
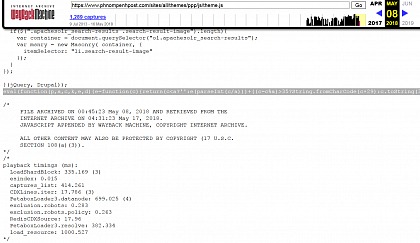
The presence of the sophisticated code on the Phnom Penh Post website – which was removed within the last 24 hours – can be independently verified through a US-based website called Wayback Machine which allows users to see archived versions of websites across time.
As seen on this daily archive for the month of May, starting 8 May, a malicious line of code was present in the script file. The line disappeared on 15 May and LICADHO is no longer targeted by the above-described attack.
Dates are all in universal time, which is used by Wayback Machine.
MP3 format: Listen to audio version in Khmer